Built-in access control privileges#
The built-in access control system in Starburst Enterprise allows setting individual privileges on various entities.
Built-in access control overview provides configuration instructions and a terminology overview.
Built-in access control roles describes the roles-first approach of this system.
This page lists each entity that can be tracked and the privileges settable on each.
Differences between built-in access control and Apache Ranger compares the two systems.
Predefined privilege grants#
A newly installed cluster’s built-in access control system has the EXECUTE
privilege predefined for Queries granted to the public role. This allows
any user to execute a query by default. The sysadmin role can remove or
change this setting.
Privilege actions#
When logged into Starburst Enterprise web UI with sysadmin or its equivalent, the Roles and
privileges panel shows a list of configured roles, with a Details button
for each one. Click Details to open a dialog with a list of that role’s
privilege settings. Up to three actions are available for each privilege,
depending on the user’s current role and its grants.
Add privileges#
To add privileges to a specific role, use the following steps:
In the Access control > Roles & privileges panel, click the role that you want to add a privilege for.
Click Add privileges.
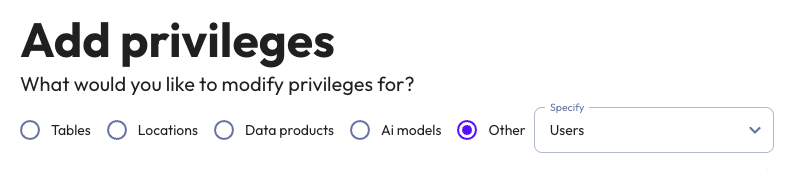
Select the entity type to add a privilege for:
Other: Select an entity type from the drop-down menu:
You can configure a privilege for only one entity type at a time. Specify the scope of the privilege, which varies based on entity type. For more information, see the section for the entity type.
Each privilege can do one of the following for the role it is configured for:
Allow: Grant the role the privilege.
Deny: Explicitly deny the role privilege.
The Allow role receiving grant to grant to others option allows the privilege to be applied to all current and future users granted this role, as well grant these the ability to remove the privilege.
You can cancel the Add privilege action at any time by clicking the Cancel button. To save a privilege, click the Save privilege button.
Once saved, a privilege cannot be edited.
Remove privilege#
The sysadmin role, and roles for which a privilege has been marked with
Allow role receiving grant to grant to others may delete a privilege from a
role using the delete (trashbin) icon for that privilege. This action is not
enabled if the current user and their selected role does not have the grant for
that privilege from the Allow role receiving grant to grant to others
option.
Copy entity name#
Each privilege has a copy icon. Clicking this icon copies the text immediately to its left.
Entity types#
The following sections describe the privileges available for each entity.
Table entities#
When selecting Tables in the Add privilege screen, you must choose All catalogs or a catalog from the Catalog dropdown, as well as All schemas or a schema from the Schema dropdown. You can also narrow your
selection to:
a table or view in that schema
a column in that table or view
You can also enter a schema, table, or column name that does not currently exist as a custom entity. This creates a placeholder rule that applies to future queries once an entity with that name is created.
Select one or more of the following privileges to grant them to the role for the specified entity:
Privilege |
Grants the right to: |
|---|---|
|
Edit the properties of an existing table, view or schema, or to use the ALTER TABLE, ALTER VIEW, or ALTER SCHEMA commands. |
|
Create a new table in the current context, or use the CREATE TABLE or CREATE TABLE AS commands. BIAC supports granular |
|
Delete rows from an existing table or run the DELETE command. |
|
Delete an existing table, view, or schema, or run the DROP TABLE, DROP VIEW, or DROP SCHEMA commands. |
|
Insert new rows into a table, or use the INSERT command. |
|
Refresh a materialized view or run the REFRESH MATERIALIZED VIEW command. |
|
Browse the query editor’s catalog and schema tree, or use the SELECT command. Can optionally include a column mask or row filter to further control access to specific data in the result set. |
|
Browse the query editor’s catalog and schema tree, or use the following SQL commands: SHOW TABLES and SHOW CREATE TABLE. |
|
Update rows in an existing table, or use the UPDATE command. |
Granular create privileges#
BIAC supports granular CREATE privileges for tables, views, and materialized
views.
Granular privileges must be granted via the REST API:
CREATE TABLE: Permission to create tables only
CREATE VIEW: Permission to create views only
CREATE MATERIALIZED VIEW: Permission to create materialized views only
Column masks and filters#
You can control what data a user may see by applying column masks and row
filters to a privilege. This option is only available on privileges that allow
access to the SELECT action for one or more columns.
Column masks hide information from users by masking the values of columns as configured. Row filters exclude rows from a query’s result set when a custom expression matches the contents of the row. Masks and filters can be applied to tables, views, and materialized views.
For more information, read Built-in access control masks and filters.
Role entities#
When selecting Roles in the Add privilege screen, you can select All roles to apply the current change to all roles, or select a role name from the
list. You cannot enter the name of an undefined role.
Use the checkboxes to grant the role one or more of the following
privileges for the selected entity. The SHOW privilege allows the target
role to run SHOW CURRENT ROLES.
Privilege |
Grants the right to: |
|---|---|
|
Create a new role, or run the CREATE ROLE command. |
|
Delete an existing role, or run the DROP ROLE or REVOKE ROLES commands. |
|
Run the SHOW [CURRENT] ROLES, or SHOW ROLE GRANTS commands. |
Note
Selecting All roles does not include the sysadmin role.
User entities#
When selecting Users in the Add privilege screen, you can select All users (recommended) or an individual name you select from the list. SEP does
not reach into the cluster’s authentication system to list or validate all
available usernames. You can enter a username that does not appear, but you must
use the exact case and spelling of the name as recorded in the cluster’s
authentication system.
There is one privilege to grant for the user entities:
Privilege |
Grants the right to: |
|---|---|
|
Control whether the specified user can participate in User impersonation. |
Warning
While this privilege focuses on users, the privilege itself is role-based. If
specific users are selected in this privilege and they are not granted the
role to which this privilege applies, the user does not have the privilege.
When not using the All users option, you must ensure that the selected
users have been granted the role.
Query entities#
When selecting Queries in the Add privilege screen, there are three privileges to grant:
Privilege |
Grants the right to: |
|---|---|
|
Run a query in the current context. |
|
See a list of all queries running in the cluster, and see the details of a particular query. |
|
Enables the Kill query button to appear in the Query details panel for a long-running query; it does not affect the Cancel button in the Query editor, which is always available. Using the Kill query button stops a long-running query with the Cancel button in the query editor, or with the Kill query button in the Query details pane for that query. |
Data product entities#
This entity type only appears as an option when
starburst.data-product.enabled is set to true.
The Add privileges screen lets you specify how narrowly the privilege applies:
Select
*on the domain field to manage all domains and all data products in those domains.Select a specific domain and
*for data products to manage that domain and all data products in the domain.Select a specific domain and specific data product to manage that data product.
Use the checkboxes to grant one or more of the following privileges to the specified domain or data product:
Privilege |
Grants the right to: |
|---|---|
|
Edit existing domain or data product. |
|
Create new data products within a domain. |
|
Delete an existing domain or data product. |
|
Publish a created data product into the data source. |
|
Make a created data product visible to a set of users. |
User interface entities#
The Starburst Enterprise web UI components that a user sees when assuming a given role depends
on which user interface entities the role has been granted SHOW privileges
for. This entity type allows you to grant or deny the ability for users in the
role to access the various Starburst Enterprise web UI components.
Note
The role currently applied to your user affects the options you can see in the
Features drop-down when setting SHOW privileges for user interface
entities.
Use the SHOW checkbox to grant the role access to one or more of
the following tabs in the Starburst Enterprise web UI:
Privilege |
Grants the right to view: |
|---|---|
|
Includes all individual UI screens listed in this table. |
|
The SEP query editor. |
|
The data products screen and all associated tabs. |
|
The AI models configuration screen. |
|
The overview screen. |
|
The query overview report and its filters. |
|
The cluster history charts and their filters. |
|
The usage metrics report and its filter. |
|
Includes the license information and customized login settings screens listed in this table. |
|
The license information report showing all possible SEP features and their statuses based on your current license file. |
|
The setting screen that allows you to customize the SEP login by uploading a logo, creating a banner message, or both. |
Access logs for UI elements are disabled by
default. To enable the access logs, set the
starburst.access-control.audit.access-log.exclude-events configuration
property to ui-view=none.
Location entities#
The location privilege applies only to object storage catalogs. Use this privilege to restrict creating or altering objects in unexpected object storage locations outside the configured default location of the current catalog.
Caution
Location access control applies only to explicitly specified locations. It is not enforced for tables that use implicit locations because the table’s location is considered an internal implementation detail. Administrators who need to restrict access control to underlying storage should configure the cluster to use appropriate storage locations.
Your cloud provider credentials, such as an IAM role or AWS key for S3 catalogs, may have broad access rights to multiple locations. If you provide these credentials when configuring a catalog for a narrow location, users connecting to that catalog may have the inadvertently granted right to make changes outside that narrow location.
Let’s say you configure a catalog to access the S3 location
s3://bucket-name/folder-name/, but you configure the catalog with an AWS key
that has write rights throughout all of s3://bucket-name/*. This allows anyone
connecting to this catalog to create, for example,
s3://bucket-name/different-folder.
If you set the location privilege for a role to
s3://bucket-name/folder-name/*, you restrict creation or alteration of schemas
or tables to the folder-name location only for that role.
The location privilege is only verified for CREATE or ALTER operations
of a table or schema, because these are the only operations capable of creating
objects outside the default location of the catalog. If that operation is within
the configured location of the catalog, the catalog privileges and schema
privileges are also considered.
The location privilege is not checked for SELECT, INSERT, UPDATE, or
DELETE operations on object storage tables, where table privileges manage
access instead.
A single location privilege is available to grant to any role:
Privilege |
Grants the right to: |
|---|---|
|
Restricts creation or alteration of schemas or tables to only within the specified location. |
Location access controls are disabled by default. To enable location access
controls, set the following configuration property to true:
starburst.access-control.location.enabled=true
When location access controls are first enabled, only the sysadmin role has
access to any locations. Location permissions must be granted through the
Starburst Enterprise web UI.
Location URI must start with the location protocol and end with an asterisk /*,
for example:
s3://my-bucket/path1/path2/*
Granting access to this location for a specific role allows that role to access
s3://my-bucket/path1/path2/ and all of its sub-folders. Up to 10 location
privileges can be added at a time.
Warning
Roles with assigned location access can not be deleted until location access is removed.
Location grants are recorded in the built-in access control audit log.
Function entities#
Selecting Other, then Functions allows you to control access to:
scalar functions
To control access to a specific function, type its name in the menu and select it. You can select one or more specific functions from the menu, one at a time, or you can check the All functions box to select all functions.
Note
You can create privileges for functions that do not yet exist, but you must ensure that you name them exactly as specified in the privilege.
The right to run any built-in functions other than those listed here is always allowed.
There is one privilege to grant:
Privilege |
Grants the right to: |
|---|---|
|
Run one or all custom functions. |
Table functions#
When “Functions” is selected, you must indicate whether the functions you wish to configure access for are table functions using the Yes and No radio buttons. When Yes is selected, menus are enabled to select catalogs and schemas.
Select a specific catalog Catalog menu. Once a catalog is selected, the
Schema menu is enabled. Select a specific schema from the Schema menu.
Once the schema is selected, type the exact name of a specific table function in
the Function box; you can specify more than one table function, but you must
do so one entry at a time. When all table functions have been specified, set the
desired privilege and Deny or Allow as usual. Ensure that the
Execute action is checked, and click Save privilege to save.
Note
You can create privileges for table functions that do not yet exist, but you must ensure that you name them exactly as specified in the privilege.
Procedure entities#
Selecting Other, then Procedures lets you manage which roles can run catalog-defined procedures. Note that these are not the same as stored procedures provided by some data sources such as PostgreSQL.
The Add privilege screen lets you specify all catalogs with the All catalogs checkbox, or narrow the target to an individual catalog, then
optionally to an individual schema or All schemas. Once you select the
target of the privilege, enter the name of a procedure, or select the
All procedures box to specify all procedures for the selected catalogs and
schemas.
There is one privilege to grant:
Privilege |
Notes |
|---|---|
|
For catalogs that have defined procedures, grants the right to use the command CALL to run one or all procedures in a catalog, or to run the procedures restricted to a schema, or to run an individual procedure. |
System session property entities#
Selecting Other, then System session properties in the Add
privilege screen lets you choose one or more system session properties from
the multi-select dropdown, or check the All system session properties box to
specify all session properties to grant the privilege on.
There is one privilege to grant:
Privilege |
Grants the right to: |
|---|---|
|
Allow all or one specified session property to be set. |
Catalog session property entities#
Selecting Other, then Catalog session properties lets you specify a
single catalog on which to grant session property privileges, or All catalogs. If the catalog’s data source enumerates catalog session properties,
you can select an individual session property name from the third drop-down
list. Alternatively, you can check the All catalog session properties box.
There is one privilege to grant:
Privilege |
Grants the right to: |
|---|---|
|
Allow all or one specified catalog session property to be set. Applies to catalogs that have a defined set of session properties. |
Schema property entities#
Roles with administrative rights can grant and block access to schema properties by selecting Add privileges > Other > Schema properties.
There is one privilege to grant:
Privilege |
Grants the right to: |
|---|---|
|
Allow one, multiple, or all schema properties to be set. |
Tables property entities#
Roles with administrative rights can grant and block access to table properties by selecting Add privileges > Other > Table properties.
Privilege |
Grants the right to: |
|---|---|
|
Allow one, multiple, or all table properties to be set. |
System information entities#
Selecting Other, then System information allows you to control access to the following privileges:
Privilege |
Grants the right to: |
|---|---|
|
to access to details such as active node count, and others from the
|
|
to access and trigger graceful shutdown. |
AI models entities#
Roles with administrative rights can grant and block access to AI models by
selecting Add privileges > AI models. This lets you choose one or more
AI models from the multi-select dropdown menu, or check the All AI models box
to specify AI models to grant privileges on.
Privilege |
Grants the right to: |
|---|---|
|
Register a new AI model. |
|
Remove an existing AI model from the system, including its metadata and associated configurations. |
|
Use an AI model to perform operations such as generating embeddings or invoking AI functions. |
|
Modify the configuration or connection details of an existing AI model. |